You are looking at the documentation of a prior release. To read the documentation of the latest release, please
visit here.
New to KubeDB? Please start here.
Reconfigure TLS MySQL
This guide will give an overview on how KubeDB Enterprise operator reconfigures TLS configuration i.e. add TLS, remove TLS, update issuer/cluster issuer or Certificates and rotate the certificates of a MySQL database.
Before You Begin
- You should be familiar with the following
KubeDBconcepts:
How Reconfiguring MySQL TLS Configuration Process Works
The following diagram shows how the KubeDB enterprise operator reconfigure TLS of the MySQL database server. Open the image in a new tab to see the enlarged version.
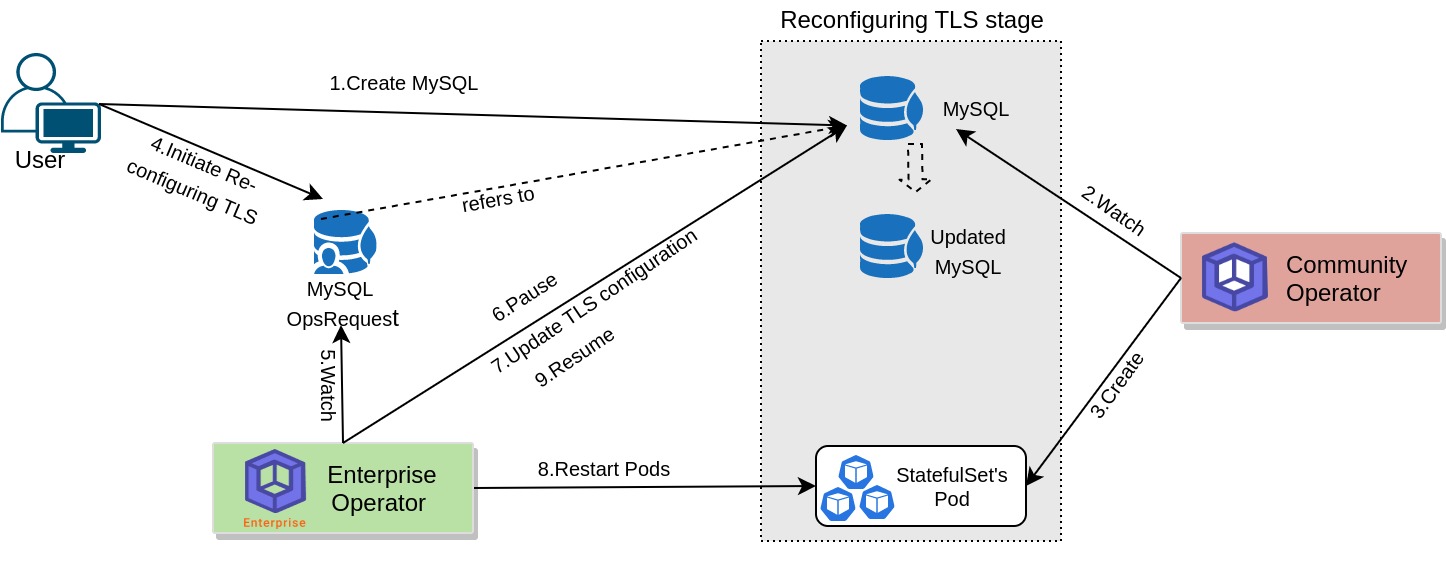
The Reconfiguring MySQL TLS process consists of the following steps:
At first, a user creates a
MySQLCustom Resource Object (CRO).KubeDBCommunity operator watches theMySQLCRO.When the operator finds a
MySQLCR, it creates required number ofStatefulSetsand related necessary stuff like secrets, services, etc.Then, in order to reconfigure the TLS configuration of the
MySQLdatabase the user creates aMySQLOpsRequestCR with desired information.KubeDBEnterprise operator watches theMySQLOpsRequestCR.When it finds a
MySQLOpsRequestCR, it pauses theMySQLobject which is referred from theMySQLOpsRequest. So, theKubeDBCommunity operator doesn’t perform any operations on theMongoDBobject during the reconfiguring TLS process.Then the
KubeDBEnterprise operator will add, remove, update or rotate TLS configuration based on the Ops Request yaml.Then the
KubeDBEnterprise operator will restart all the Pods of the database so that they restart with the new TLS configuration defined in theMongoDBOpsRequestCR.After the successful reconfiguring of the
MySQLTLS, theKubeDBEnterprise operator resumes theMySQLobject so that theKubeDBCommunity operator resumes its usual operations.
In the next docs, we are going to show a step-by-step guide on reconfiguring tls of MySQL database using reconfigure-tls operation.



































