You are looking at the documentation of a prior release. To read the documentation of the latest release, please
visit here.
New to KubeDB? Please start here.
Reconfiguring TLS of Druid
This guide will give an overview on how KubeDB Ops-manager operator reconfigures TLS configuration i.e. add TLS, remove TLS, update issuer/cluster issuer or Certificates and rotate the certificates of Druid.
Before You Begin
- You should be familiar with the following
KubeDBconcepts:
How Reconfiguring Druid TLS Configuration Process Works
The following diagram shows how KubeDB Ops-manager operator reconfigures TLS of a Druid. Open the image in a new tab to see the enlarged version.
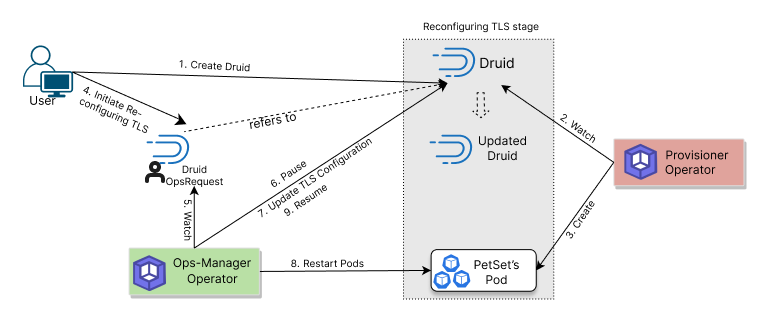
The Reconfiguring Druid TLS process consists of the following steps:
At first, a user creates a
DruidCustom Resource Object (CRO).KubeDBProvisioner operator watches theDruidCRO.When the operator finds a
DruidCR, it creates required number ofPetSetsand related necessary stuff like secrets, services, etc.Then, in order to reconfigure the TLS configuration of the
Druiddatabase the user creates aDruidOpsRequestCR with desired information.KubeDBOps-manager operator watches theDruidOpsRequestCR.When it finds a
DruidOpsRequestCR, it pauses theDruidobject which is referred from theDruidOpsRequest. So, theKubeDBProvisioner operator doesn’t perform any operations on theDruidobject during the reconfiguring TLS process.Then the
KubeDBOps-manager operator will add, remove, update or rotate TLS configuration based on the Ops Request yaml.Then the
KubeDBOps-manager operator will restart all the Pods of the database so that they restart with the new TLS configuration defined in theDruidOpsRequestCR.After the successful reconfiguring of the
DruidTLS, theKubeDBOps-manager operator resumes theDruidobject so that theKubeDBProvisioner operator resumes its usual operations.
In the next docs, we are going to show a step by step guide on reconfiguring TLS configuration of a Druid database using DruidOpsRequest CRD.



































